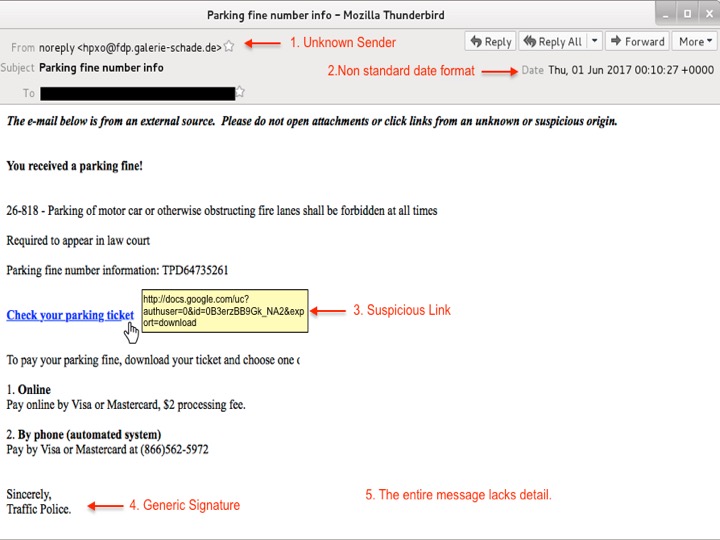
Can you recognize the social engineering red flags?
The social engineering of end-users makes up the largest surface area of attack and is often the most neglected part of cyber security. A simple “healthy level of paranoia” can positively change this human threat landscape into “Human Firewalls.”
In 2015, Jennifer Johnson wrote an article concerning phishing emails that caught my attention.”Spear Phishing: How Employees Can Be a Defense to Cyber Attacks.” The focus of the article is to train employees to effectively become an integral part of any company’s cyber security strategy.
Scan the following popular phishing message to see if you can recognize at least 5 of the 22 red flags indicate a social engineering attack attempt.
Scroll down to see the 5 most common flags.
1. If an email message is coming from an unknown sender – question it!
2. If a message has a nonstandard date/time format – question it!
3. If an email contains an attachment or link that you are not expecting or looks suspicious – question it! (Hover over links to verify where it is taking you.)
4. If a message signature is unspecific – question it!
5. If a message lacks general detail – question it!
Click the following link to download a FREE .pdf file with all of the 22 red flags that we educate employees to recognize in any phishing message. SocialEngineeringRedFlags
To set up training for your team please contact:
Mark Brandon, Sr. Vice President of Business Operations
Phone: 804-379-1800
Email: mbrandon@thinknts.com